The primary option is -x509: it forces the openssl req command to generate a root certificate instead of a certificate signing request:
openssl req \
-days 99999 \
-keyout .key \
-new \
-nodes \
-out .crt \
-sha256 \
-x509
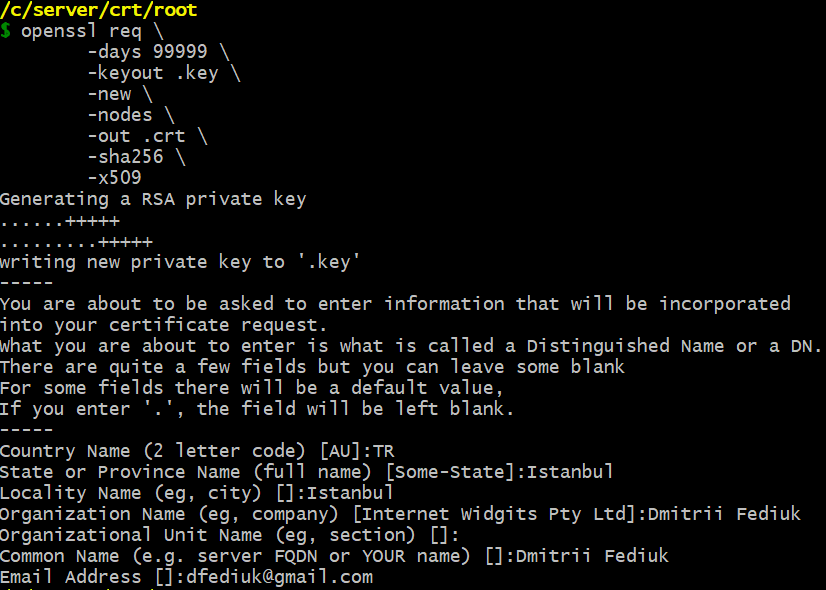
-
daysn
When the -x509 option is being used this specifies the number of days to certify the certificate for.
The default is 30 days.
-
keyoutfilename
This gives the filename to write the newly created private key to.
-new
Normally, this option generates a new certificate request.
But in my case, it does not generate a new certificate request because I use -x509 alongside with -new.
In my case the -new option generates a new RSA private key because I do not use the -key option.
The private key is generated with the default length: 2048 bits.
-nodes
If this option is specified then if a private key is created it will not be encrypted.
-outfilename
This specifies the output filename to write to or standard output by default.
-sha256(-digest)
This specifies the message digest to sign the request with (such as -md5, -sha1).
This overrides the digest algorithm specified in the configuration file.
Some public key algorithms may override this choice.
For instance, DSA signatures always use SHA1, GOST R 34.10 signatures always use GOST R 34.11-94 (-md_gost94).
-x509
This option outputs a self-signed certificate instead of a certificate request.
This is typically used to generate a test certificate or a self-signed root CA.
The extensions added to the certificate (if any) are specified in the configuration file.
Unless specified using the set_serial option, a large random number will be used for the serial number.